Overview
Products and Software applications reach the end of their Life Cycle for a number of reasons. These reasons may be due to market demands, technology innovation and development driving changes in the product or the products simply mature over time and are replaced or refresh by functionally richer technology.
Six major security issues support timely life cycle replacement of systems and applications:
- Outdated hardware systems are vulnerable to attacks and hacking.
- Older systems don't have adequate security locking and password functionality.
- Security fixes and vulnerability patches are often no longer available for older systems.
- Older operating systems often don't contain the necessary tools to identify and remedy system compromises.
- The risk of system compromise via Instant Messaging attacks is greater with outdated equipment.
- The overall security risk for older systems is increased due to a lack of available technical support and defensive measures.
Security is an important driver for Life Cycle planning. UBCIT has set out an end-of-life plan by classifying computer systems and its supporting business applications by categorizing their level of importance as Mission Critical, Core System, Essential or Important. This approach will help UBCIT better manage responses to issues reported on computer systems operations, security and business applications which are critical to UBC’s operations, its reputation and survival.
University of British Columbia Information Technology (UBCIT) recognizes that end-of-life milestones often prompt organization like UBCIT to review the way in which such end-of-life milestones impact UBC’s daily operations and security. This accords UBCIT to stay vigilant for rich secure technology to feed the demanding thirst for faster data transfer speed and reliability in its networked infrastructure.
Use of Definitions
- Life Cycle: The period of time, during which information technology hardware and business application remains useful to UBCIT and its clients.
- System Classification is a prioritization and identification schema that allows UBCIT and its technical support groups to better understand the criticality of its client’s daily productivity requirements and accords confidence in UBCIT to provide a strong and reliable computer network.
- Refresh Rate: The planned rate of replacement for information technology hardware and Application software and databases identified as Mission Critical, Core or Essential Systems to UBC’s reputation and survival.
Scope
Business Assessment is separated into two constituents, Risk Assessment and Business Impact Analysis (BIA). The Risk Assessment is intended to measure present vulnerabilities to the business’s environment, while the Business Impact Analysis evaluates probable loss that could result during a system failure or disaster.
Key Drivers
- Identify how quickly essential business units and/or application processes have to return to full operation following a disaster situation.
- Delineate the business impact of disaster impact scenarios on the ability to deliver product or to support mission-critical services.
Understanding the Life Cycle Relationship
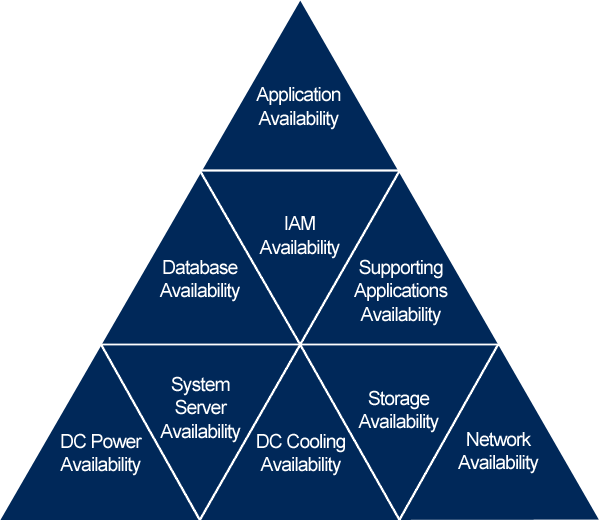
For 99% user availaibility requires that the components in the chart above follow the same 99% life cycle monitoring cycles to enable a strong foundation at UBC IT.
Life Cycle Plan Approach
The following will be used by UBC IT to classify a system based on importance to UBC. System refers to a software application along with the entire supporting infrastructure that it is dependent upon (e.g. computer hardware, system software, applications, networks, data, utilities, etc.).
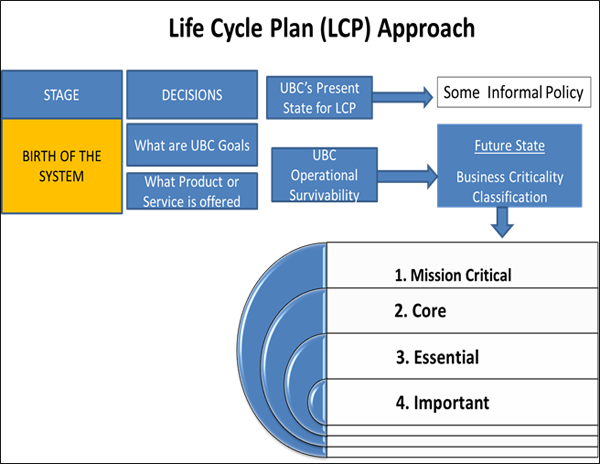
System Classification
1. "Mission Critical"
System is “Mission Critical” for UBC to remain operational exhibiting most of the following characteristics:
- Critical to the health or safety of students, staff, or faculty
- Will threaten the ongoing viability of UBC and/or its reputation if service is compromised for more than 1 hour
- Will cause major legal, compliance or regulatory ramifications if service is compromised for more than 1 hour
2. "Core"
System is "Core" in delivery of IT service to UBC or for UBC to remain operational exhibiting most of the following characteristics:
- High chance of threatening the ongoing viability of UBC and/or its reputation if service is compromised for more than 4 hours
- High chance of major legal, compliance or regulatory ramifications if service is compromised for more than 4 hours
- Critical component in providing academic, administrative, or medical operations
- Outage impacts more than one area/system (from "Important" to "Mission Critical")
3. "Essential"
System is "Essential" to UBC exhibiting most of the following characteristics:
- Chance of threatening the ongoing viability of UBC and/or its reputation if service is compromised for more than 1 day
- Chance of major legal, compliance or regulatory ramifications if service is compromised for more than 1 day
- Generates daily financial revenue = to or > $250,000 Outage impacts more than one area
4. "Important"
System is "Important" to UBC exhibiting most of the following characteristics:
- Chance of threatening the ongoing viability of UBC and/or its reputation if service is compromised for more than 5 days.
- Chance of major legal, compliance or regulatory ramifications if service is compromised for more than 5 days
- A value add from Important to Mission Critical
